We’re all aware that bad people exist on the Internet who want to steal our personal information for whatever nefarious reason they may have. Sometimes they want our bank account login, which makes sense, but other times they want something else, such as a Facebook login, which makes less sense. Whatever motivates these people, any attempt they make to effectively trick you into providing the information they seek is referred to as “phishing.”
Phishing takes many forms; we’ll go over the most common ones and provide you with the knowledge you need to identify and protect yourself from these attempts, both online and in person.
What Exactly is Phishing?
In practice, phishing is the attempt to trick someone into providing personal information (such as account credentials, credit card numbers, or other sensitive information) by falsely presenting yourself as a trustworthy institution or individual who requires the information for legitimate reasons.
A simple example of phishing would be as follows:
- I get an email with my bank’s logo at the top that says my password has been disabled due to multiple failed login attempts. It states that the security of my account is very important to them and that I must now restore access to my account by clicking on the link below.
- When I click on the link, it takes me to a website that looks exactly like my bank, so I enter my username and password. But then it doesn’t log me in; instead, it may display some kind of error, but it doesn’t really matter at this point because…
- I’ve now given a phisher my bank account credentials; they can instantly log into my account, change the password to lock me out, and steal my life savings.
Here is an example of a phishing text:
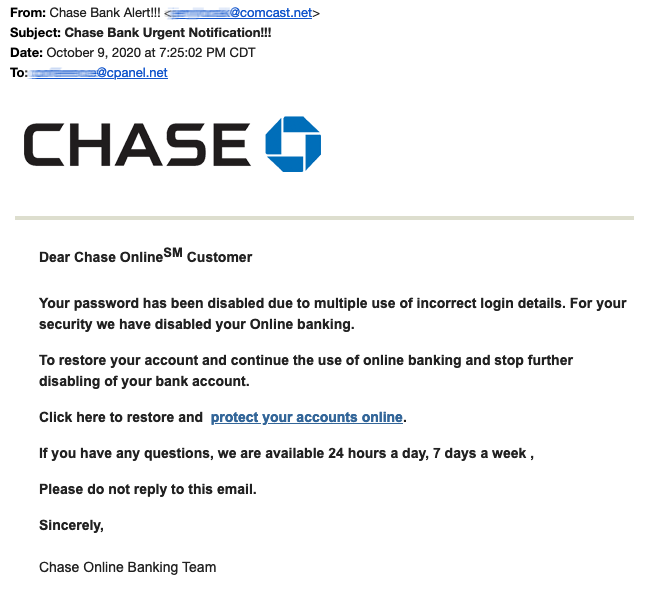
That is, in a nutshell, how phishing works. Though these scams have become more sophisticated over time, including attempts via text message and phone: “Hello, this is your bank calling.” We need to talk about something important with you about your account, but first, we need to confirm your identity. Please enter your username and password…”, the overall goal and execution of these scams remain essentially the same.
How to Protect Yourself From Phishing
As you can see, phishers have a variety of methods to try to trick you, but there are some fundamental things to remember that will protect you and prevent any phisher from taking advantage.
- Always think about the source. That email from “your bank” requesting your account credentials is most likely coming from an email address unrelated to your or any bank. Here’s a closer look at the email we showed you earlier, with the sending email simply being a random email address:
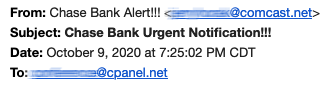
- Remember to always consider the source. Consider it as a phishing call if “your bank” calls you and requests sensitive information. If, on the other hand, you call your bank, you are the source, and you may be able to provide account-specific information related to the reason for your call.
- Never, ever click on any links in suspicious-looking emails. These links may occasionally contain executable files that compromise whatever device you were using when you clicked.
- Use your best judgment. If something appears to be off, it is most likely a phishing attempt. Misspelled words, poor grammar, and unusual phrases in emails from “legitimate” businesses are examples of this.
When in doubt, the best bet is often to contact the alleged sender directly; call your bank and ask if they sent you that email. It is always better to be safe than sorry.
If you ever receive a phishing email claiming to be from cPanel or redirecting you to a cPanel login page, please forward it to [email protected] along with the full email headers so we can properly investigate the phishing attempt.
To learn more about phishing, go to https://www.consumer.ftc.gov/articles/how-to-recognize-and-avoid-phishing-scams.

