Today we are going to talk about Imunify360, and how to secure your website with it.
The security of a website is like that of a house. The more solid and robust the foundations are, the safer the building will be. And this is the reason why today I come to talk to you about Imunify360, a software that has arrived with a bang and that we have adopted in all our hosting plans.
But what is Imunify360? How does this software protect my website?
If you have never worked with this tool on your hosting or want to know in depth how it works, in this post I explain it to you in detail.
Will you accompany me?
Table of Contents
What is Imunify360?
Imunify360 is a web security software that incorporates advanced functions for the prevention and detection of malware, as well as the prevention of attacks through automatic security rules (failed session attempts, IPs, and suspicious events…).
Likewise, Imunify360 was one of the first firewalls to incorporate AI (Artificial Intelligence) with the aim of mitigating and even blocking threats that could put your website at risk.
This security software is developed by CloudLinux, considered the most advanced for web environments and applications. This security software is developed by CloudLinux, the operating system used by all our web hosting and CMS Hosting plans, and is currently considered the most advanced for web environments and applications.
How does Imunify360 protect my website?
To offer the highest security standards, Imunify360 focuses its defense on 7 layers of protection that are:
- Advanced Firewall
- CAPTCHA system
- Intrusion detection system (IDS/IPS)
- Malware scanning and cleaning
- proactive defense
- KernelCare
- Reputation management.
Advanced Firewall
Imunify360 uses a herd immunity system and Artificial Intelligence (AI) with the aim of keeping web servers safe from any threats such as brute force attacks (DoS, DDoS) or malicious code injection attacks.
To do this, Imunify360 has the best WAF (Web Application Firewall) on the market, which allows you to analyze web traffic throughout the request, both at the level of the web address visited, parameters sent, or even headers sent in the web request.
This tool also has thousands of mod_security rules, which protect your site against the most common vulnerabilities. In this way, if your website has a plugin or component that has not been updated, it is most likely that there is a rule that prevents the exploitation of that vulnerability and, as a consequence, prevents your website from being attacked.
Furthermore, as there is a great team behind this tool, it allows these mod_security rules to be constantly updated in order to further reinforce security.
I’ll give you an example so you can see it much more clearly. If you are working with WordPress version 5.5 and a vulnerability is detected, it is not the same for the Imunify360 team to release mod_security rules in four hours as for them to do so in six days. The exposure of your website to this security breach is much greater and the risk to your site is multiplied.
CAPTCHA system
Another feature of Imunify360 is that it integrates an advanced CAPTCHA system to detect if the traffic you receive on your website is real or comes from a robot.
But how do you achieve it?
This tool not only analyzes the requests made by the supposed user on your site, but with the help of the WAF, the mod_security rules, or, for example, failed access attempts in the WordPress admin, Imunify360 is able to detect if it is a bot a real person who is browsing your website.
And what happens after this analysis?
If no strange activity is detected, Imunify360’s behavior is completely transparent to the user. It will not affect the navigability of the page in any way, nor, therefore, does it affect the user experience.
In other words, if the person browsing is a real user, nothing happens.
On the other hand, if Imunify360 detects that it is a bot that is making requests or a malicious user trying to access your site by brute force, it will show a CAPTCHA as a barrier to prevent it from doing its thing.
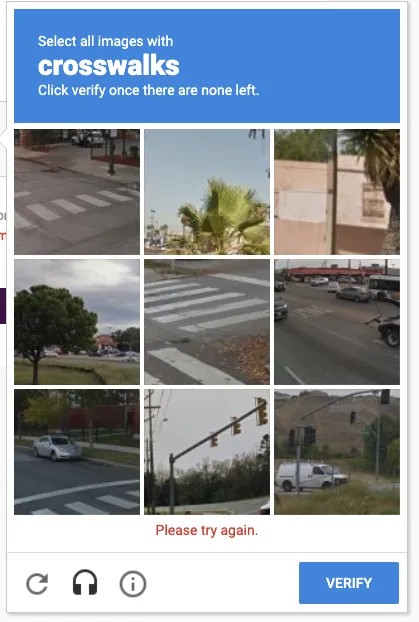
Do you want to see a real example? We have tried to access the administration panel of a test WordPress hosted on our servers and, after entering the password incorrectly several times, a CAPTCHA like this is automatically displayed for you to confirm that you are not a bot. If you do not complete the CAPTCHA, the bot will not be able to continue browsing through this IP:
Intrusion detection systems (IDS/IPS)
Another of Imunify360’s strong points is its intrusion detection and prevention system.
This system is made up of a global database of attackers and uses it to block them before these malicious users reach your site. It also scans and blocks suspicious IP addresses for multiple invalid login attempts, potential exploits, and other security threats.
Malware scanning and cleaning
One of the most common security problems on a website is the existence of malware. To prevent and eliminate it, Imunify360 performs periodic scans of your entire website in search of files that may have been infected with malicious code.
Once Imunify360 detects that a file is infected, it automatically attempts to clean it. That is why, normally, you will see the following statuses in your Imunify360 panel:
- Cleaned – This is a file with malicious code that Imunify360 was able to clean.
- Deleted: This is a file that only had malicious code and you deleted it completely.
- Infected – Imunify360 may not have been able to complete the cleanup, so it is recommended that you review the file manually. Of course, keep in mind that, while the scan is being performed, all detected files will be displayed in this state, so it is important that you look at the date on which the event (or file) was detected.
Proactive defense
If there is anything that differentiates Imunify360 from other software packages, it is precisely this.
Imunify360 is able to detect malicious code that scanners are unable to find.
And how does he do it? Well, Imunify360 not only performs malware scans based on the content of the files on a website but also analyzes their behavior.
To make it clearer, I’ll give you an example. Imagine that you have a file on your website that does not contain malicious code, but does execute a script that allows a user to access your website’s control panel as an administrator. This would pass the malware scan since there is no harmful content, but lmunify360 would block it anyway since what the file does can put the security of your website and your business at risk.
KernelCare
Another strong point of Imunify360 is that it is capable of keeping the server kernel secure and patching it automatically, without the need to restart the service which could leave your website inoperative for a few minutes, even hours.
What does this translate into? In a secure and stable web hosting service, in which maintenance and security tasks do not have any negative impact on the performance of your site.
Reputation Management
Finally, the management of the reputation of domains or IP addresses. Daily, Imunify360 checks to see if your site or the IP addresses of the server you are hosted on have been blocked or moved to a blacklist.
And I explain the importance of this… If you have, for example, an SSD Hosting plan or WordPress Hosting, whether with us or any other provider, you are sharing the IP address with other users. Imagine that one of those users sends massive spam messages from her account and ends up on Google’s blacklists… Do you know what that can mean for your website? You could disappear from the results pages.
That is why daily monitoring of the reputation of our IPs is essential not only to maintain the security of your site but also to take care of your SEO positioning.
Do I really need hosting with Imunify360?
It is not an obligation, of course, but if you are concerned about the security of your website, it is one of the aspects that you should take into account when purchasing a hosting plan.
Remember some of the things it can do for your website:
- Protects you against brute force attacks, the most common on shared hosting platforms.
- It includes self-learning software for advanced malware detection.
- It obtains data from the global network to block possible attacks, even before they reach your website.
- Protects web applications such as WordPress, PrestaShop, Drupal, or Joomla from malware injections.
- It includes an advanced CAPTCHA system that detects if the activity on the web is real or comes from a bot.
- Analyze access logs to cPanel, email, FTP, etc. for the detection of brute force attempts.
- If you have infected code, Imunify360 automatically cleans it
- Analyzes the execution of PHP files or possibly malicious code in real-time.
- And a thousand more things!
Imunify360 on Harmonweb
You already know that at Harmonweb we always rely on the latest technology, which is why all our hosting plans use CloudLinux as the operating system and Imunify360 to further enhance the security of your website and your business:
In fact, in your hosting control panel, you will see that you have this tool enabled so that you can monitor all Imunify360 activity yourself and ensure that your site is safe from any threats. Specifically, from the desktop you can:
- See in real-time if there are suspicious or quarantined files.
- Review action history.
- Edit the list of paths or files that you want to be ignored.
- View events that have been detected thanks to the Proactive Defense feature.
Do you want to know how it is managed? Let’s see then all the options that we have available in the Imunify360 dashboard.
How does Imunify360 work?
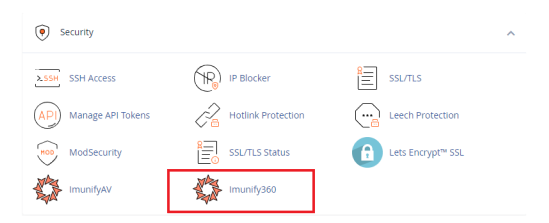
To see how the dashboard of this tool works, first access cPanel and, in the “Security” section, click on “Imunify360”.
Next, a new screen will open in which you have 4 different tabs:
- Files
- Record
- ignore list
- proactive defense
Let’s see what each of them is for.
Files Section
As soon as you land on the Imunify360 control panel you have access to a view with a summary of the latest activity of this tool, something very similar to this:
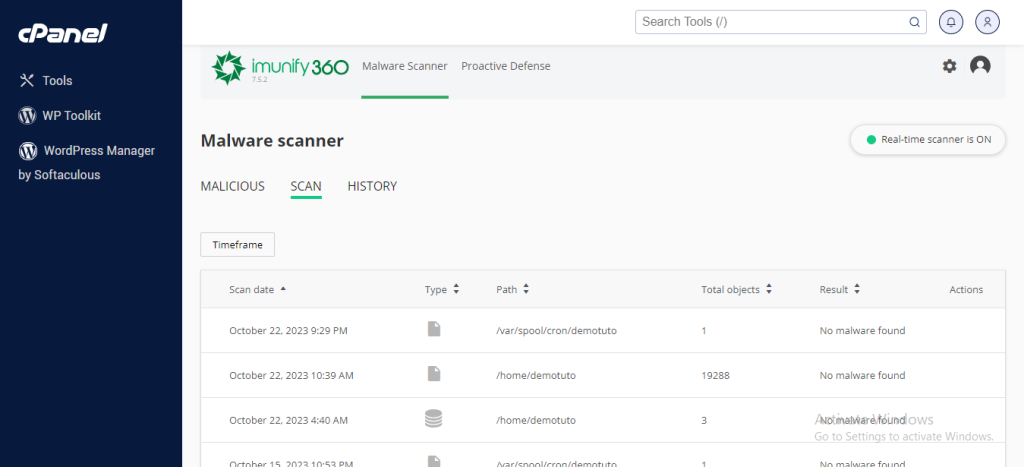
In the event that it has not detected any suspicious items, this screen will not show any results.
On the other hand, if malware has been detected (as in this example), all files and the status of each of them (cleaned, deleted, or infected) will be listed. Note that, if you need, you can filter and sort files by date or status.
What if Imunify360 detects a false positive and deletes a file that I need? Although it is not very common, it can happen. In that case, you have nothing to worry about. You already know that all our hosting plans include Codeguard Backup, a tool that allows you to download or restore complete backups, databases, applications, or email accounts in just a few clicks.
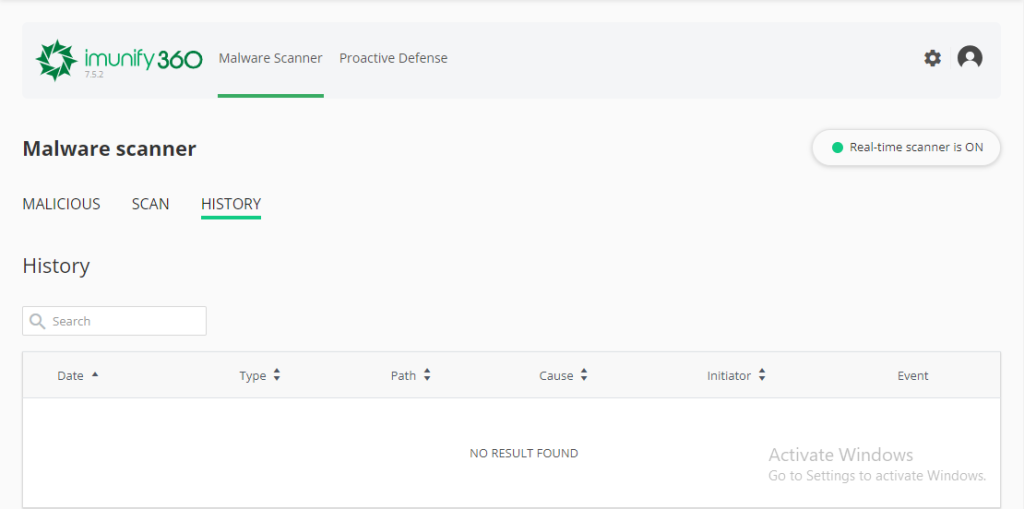
History Section
From this tab, you can check all Imunify360 activity. The dates the event was detected, time, route, status, and who started the cleanup process.
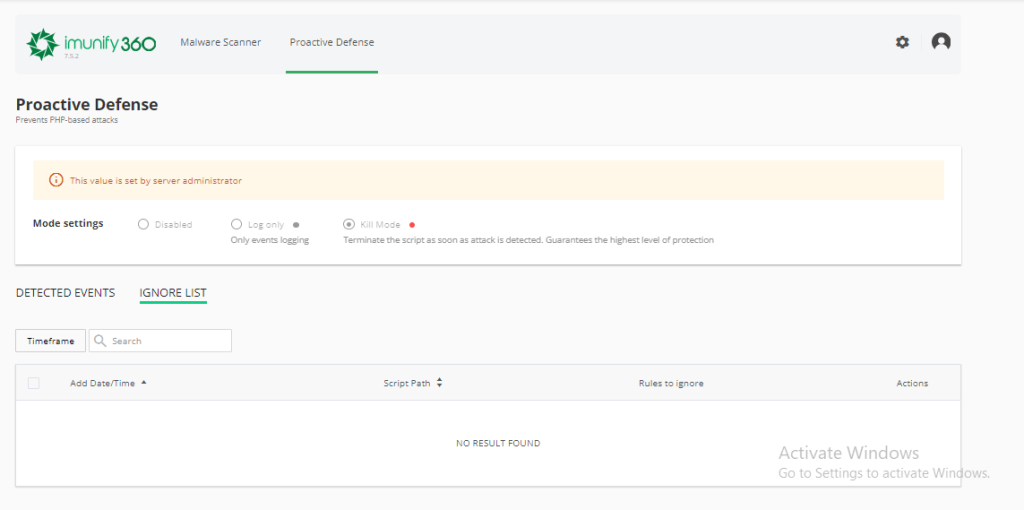
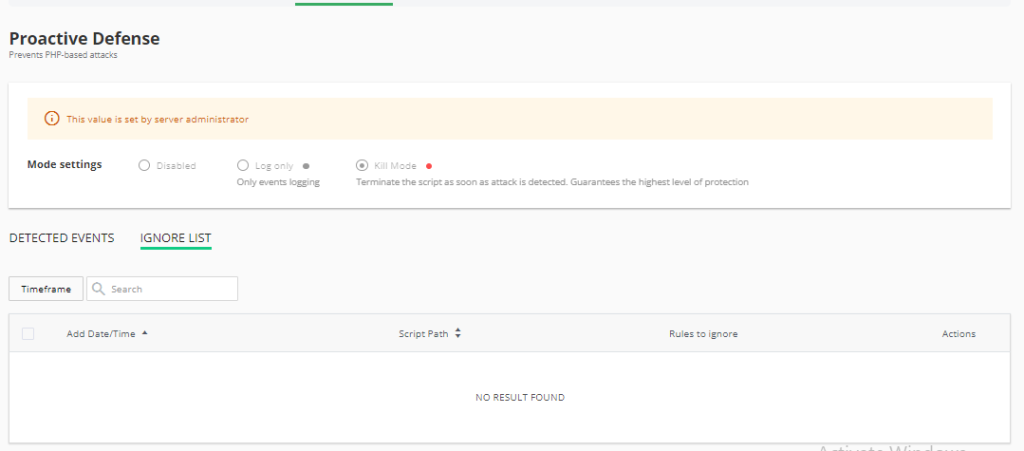
Ignore list
In this section, you can add the files that you do not want Imunify360 to scan. Obviously, I do not recommend that you include malicious files in this list, since you would be compromising the security of your website.
I only recommend using it for specific cases if, for example, you are carrying out a security audit on a plugin and you prefer that Imunify360 not scan or make modifications to them. It can also be useful when you detect a false positive.
Proactive defense
Remember how I told you this was one of the most powerful features of Imunify360? Well, in this section, you will be able to see the files it detects, and that can execute a harmful action on your website.
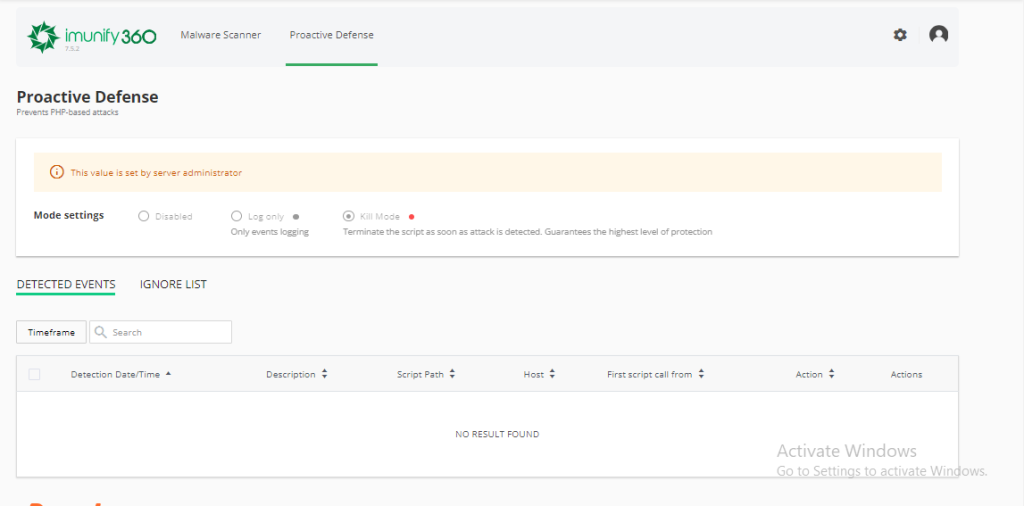
By default, Imunify360 collects all detected event logs and shows them to you here. If you want it to delete them automatically, you have to select the “Delete Mode” option.
If you believe that the detected event is a false positive and you want to send it to the ignore list, you can do so by clicking on the “Actions” icon – “Ignore detected rule for the file”. It will automatically be added to the list and that rule will not be applied again.
There is also the option that there are other rules that are marking the file as suspicious, in that case, you must select the action “Ignore all rules for the file.”
Conclusion
When it comes to security, we never take any chances, that’s why we work with Imunify360 on all our hosting plans. One of the most powerful software packages in web security, thanks to all the features it offers:
- Advanced Firewall (DDoS Protection, WAF,…)
- captcha system
- Intrusion detection systems (IDS/IPS)
- Malware scanning and cleaning
- proactive defense
- KernelCare
- reputation management
Remember that, from the control panel of all our Web Hosting plans, you have an option enabled to directly access the Imunify360 control panel to review and manage all the options that this tool gives you.
Now is your turn! What do you think of Imunify360? Have you ever worked with this tool? Tell us about your experience.


[…] our Reseller Hosting plans, in addition to all accounts being independent of each other, they have Imunify360, the most advanced web security software that incorporates functionalities for the prevention and […]
[…] performing this simple practice, you save yourself all the stress and keep your site safe from security breaches and malicious […]